The digital world is fraught with cyber threats. For those wishing to browse the internet securely and privately, a Virtual Private Network (VPN) is a vital tool. But what is a VPN?
A VPN offers a private network connection over a public network, providing an encrypted tunnel for your data to pass through, thereby safeguarding your online activities from prying eyes.
In this comprehensive guide, we’ll delve deep into VPN meaning, how it works, its types, and why you need one.
What Is a VPN?
A Virtual Private Network, commonly known as a VPN, is a secure method for accessing the internet and maintaining online privacy.
Essentially, it serves as an encrypted tunnel between a user’s device and the internet, shielding the user’s browsing activity from prying eyes on public Wi-Fi, and even from Internet Service Providers.
So when asking “what is a VPN?“, it is important to understand that it is a tool designed to enhance your online security and privacy.

VPNs work by masking the user’s IP address and swapping it with one from the VPN provider. This process of IP masking provides the effect of the user appearing to be in a different location, which can be beneficial not only for privacy but also for accessing content that may be regionally blocked.
Additionally, because your data is encrypted, VPNs provide a level of security against cyber threats such as hackers and malware.
The use of a VPN can be crucial for businesses as well, enabling employees to securely access the company’s internal network from outside the office. This adds an extra layer of protection to sensitive company information from potential cyber threats.
Furthermore, VPNs can also prevent websites and advertisers from tracking your online activity, thus giving you a more private browsing experience.
How Does a VPN Work?
A VPN operates by establishing a secure, encrypted connection between your device (a laptop, smartphone, or tablet) and a VPN server.
This secure connection called a VPN tunnel, masks your Internet Protocol (IP) address, making your online actions virtually untraceable.
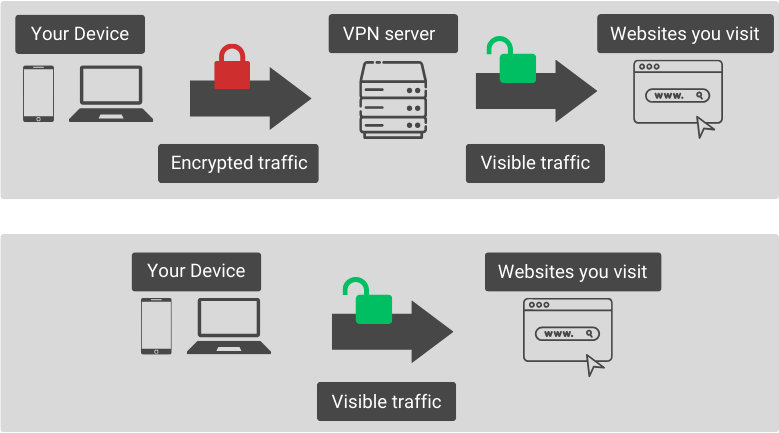
The process begins when your device connects to a VPN server. This connection is encrypted, meaning that the data being sent and received is encoded in a way that only your device and the VPN server can understand.
The VPN server then sends your encrypted data over the internet.This encryption is what makes a VPN connection private.
Since your data is encrypted, even if someone manages to intercept your data, they won’t be able to understand it.
In addition to encryption, a VPN also changes your IP address, further enhancing your online anonymity.
Benefits of Using a VPN

The following are some of the many benefits of using a VPN:
- Enhanced Security: One of the foremost benefits of using a VPN is that it boosts your online security. By encrypting your data, it protects your personal or business information from hackers and cybercriminals.
- Privacy Protection: A VPN safeguards your privacy by hiding your IP address. This makes it difficult for online trackers to monitor your browsing habits and personal information.
- Bypass Geo-Restrictions: With a VPN, you can access content that may be blocked in your region due to geo-restrictions. This is because a VPN enables you to appear as though you’re browsing from a different location.
- Safe Public Wi-Fi Use: Using public Wi-Fi networks can expose your device to various security threats. A VPN provides an added layer of protection, making it safe for you to use public Wi-Fi.
- Prevents Bandwidth Throttling: ISPs often throttle bandwidth when they detect heavy data usage. A VPN prevents this by hiding your online activity.
- Improved Remote Access: For businesses, a VPN provides secure remote access to the company network. This allows employees to work safely from any location.
Why You Need a VPN
The primary purpose of a VPN is to provide a secure and private connection to the internet. Let’s delve into the specifics of what a VPN is used for.
Public Wi-Fi
The necessity for using a Virtual Private Network (VPN) when connected to public Wi-Fi cannot be overstated.
Public Wi-Fi networks, while convenient, are notoriously insecure and expose users to a myriad of potential threats. A VPN serves as a crucial protective layer in such circumstances.

Public Wi-Fi networks are usually unencrypted, making it easy for cybercriminals to intercept sensitive data that is transferred over the network.
This can include personal information such as passwords, credit card numbers, and other confidential data.
The use of a VPN creates a secure tunnel for your data to pass through, effectively encrypting your information and making it much more difficult for unauthorized individuals to access.
Moreover, a VPN masks your IP address, making it significantly harder for third parties to track your online activities.
This ensures that your browsing habits remain private and reduces the risk of targeted attacks. The VPN acts as an intermediary between your device and the internet, thereby hiding your identity and location.

In a world where data breaches are becoming increasingly common, it is essential to take proactive measures to protect our digital footprints.
Using a VPN when connected to public Wi-Fi is one such measure that can significantly reduce the risk of falling victim to cybercrime.
It provides a much-needed shield against unwanted intrusions and helps maintain the confidentiality of your online activities.
Therefore, employing a VPN while using public Wi-Fi is not just recommended, but necessary for preserving your online security and privacy.
Traveling
Using a Virtual Private Network (VPN) while traveling can provide you with an additional layer of security, ensuring that your sensitive information remains private even when connecting to public Wi-Fi networks.

When you connect to the internet via a VPN, your data is encrypted, making it unreadable to anyone who might be attempting to intercept it.
This is particularly important when connecting to public Wi-Fi networks, such as those found in hotels or cafes, which are often not as secure as private networks.

Moreover, using a VPN while traveling can also help you bypass geographic restrictions on certain websites or online services.
Some countries may block access to specific sites or services, but with a VPN, you can appear as though you’re browsing from a different location, enabling you to access your favorite content without interruption.
Browsing the Web
Utilizing a Virtual Private Network, or VPN while browsing the internet, is crucial for a myriad of reasons. Primarily, a VPN serves to protect your privacy and security online.
In today’s digital age where cyber threats have become increasingly prevalent, it’s important to take precautions to safeguard your sensitive data.

A VPN accomplishes this by creating a secure, encrypted tunnel between your device and the server you are connecting to.
This means that any data you transmit over this connection is protected from prying eyes, making it nearly impossible for hackers, your internet service provider, or even government agencies to monitor or intercept your online activities.
Using a VPN while browsing the web also opens up a world of possibilities when it comes to accessing content that may be restricted in your region.

It achieves this by masking your actual IP address and replacing it with one from a different location. This makes it appear as though you are browsing from somewhere else, allowing you to bypass geographical restrictions and censorship.
Whether you’re trying to stream content from another country or access websites that are blocked in your region, a VPN can provide the solution.
Gaming
Using a VPN while gaming has increasingly become a prerequisite rather than an option for many serious and casual gamers alike.
For gamers, enhanced security can protect against potential threats like DDoS attacks, which can disrupt gaming sessions and negatively impact overall gaming experience.

Utilizing a VPN while gaming can also overcome geographical restrictions. Many games and gaming servers are region-locked due to various reasons such as licensing agreements or beta testing. This means that players in certain regions may not have access to these games or servers.
A VPN can solve this issue by masking the gamer’s actual location and making it appear as if they are playing from a region where the game or server is accessible.
Furthermore, a VPN can potentially provide better ping times and reduced lag. This is possible because a VPN allows gamers to connect to servers that are closer to the game servers, thereby reducing the distance that data has to travel.

This can result in smoother gameplay, which is particularly beneficial for competitive gamers where every millisecond counts.
Lastly, using a VPN while gaming can ensure an uninterrupted gaming experience even when using public Wi-Fi networks.
These networks are often unsecure and pose risks such as data theft and malware attacks. A VPN encrypts data, making it unreadable to potential hackers and thus preserving the integrity of the gamer’s personal information.
Shopping
Online shopping has become the norm in today’s digital age, providing convenience and flexibility to consumers worldwide.
However, it also poses significant risks, particularly related to online security and privacy. This is where a Virtual Private Network, or VPN, comes into play.
Using a VPN while shopping is crucial in maintaining your online safety and ensuring a secure shopping experience.

A VPN provides an added layer of security by encrypting your internet connection. It works by creating a secure tunnel through which your data travels, effectively shielding it from potential prying eyes.
This is particularly useful when conducting financial transactions online, like when you’re shopping.
Unprotected connections can expose your sensitive information such as credit card details, leaving you vulnerable to cyber threats like identity theft and fraud.
In addition to security, using a VPN while shopping can also offer other benefits such as bypassing geo-restrictions.
Some online stores display different prices for the same product based on the location of the shopper. With a VPN, you can change your virtual location, potentially unlocking better deals and saving money.
Furthermore, a VPN can help maintain your privacy by masking your IP address. This prevents online retailers from tracking your browsing habits and personalizing prices based on your shopping behavior.
Without a VPN, retailers can use this information to inflate prices on products that you have shown interest in, which could lead to you paying more than necessary.
Streaming
Using a VPN while streaming media has become increasingly crucial in today’s digital era. A VPN, or Virtual Private Network, is a service that provides an encrypted connection to the internet.
It ensures the privacy and security of your online activities by hiding your IP address and encrypting data between your device and the VPN server. This safety mechanism has significant implications when it comes to streaming content online.

One of the primary reasons to use a VPN while streaming is to bypass geographical restrictions on certain websites or streaming platforms.
Many popular streaming services, such as Netflix and Hulu, have geo-restrictions in place due to licensing agreements, which means that some content is only available in specific regions.
A VPN can mask your IP address, making it appear as if you’re accessing the internet from a different location, thereby allowing you to access region-specific content regardless of your actual location.

Another compelling reason to use a VPN while streaming is to maintain your privacy and security. Streaming platforms often collect user data, including viewing habits, which can be shared with third parties for targeted advertising.
By using a VPN, you can prevent these platforms from collecting your personal data, thereby ensuring your online privacy.
Types of VPNs
There are several types of VPNs, each catering to specific needs. The two most common ones are:
Remote Access VPN
A Remote Access VPN, or Virtual Private Network, is a technological solution that allows users to secure their data and privacy while accessing a public or private network from a remote location.
The key function of a Remote Access VPN is to create a secure tunnel between the user’s device and the VPN server.
This encrypted tunnel ensures that any data passed between the two endpoints is secure from external threats such as cybercrimes and data breaches.

A user utilizing a Remote Access VPN can transmit data as if their computing devices were directly connected to the private network.
This is achieved by masking the user’s IP address with one from the VPN server, making it seem as if the user is accessing the internet from a different location.
This feature not only enhances security but also enables users to bypass geo-restrictions imposed on various internet contents.

The implementation of a Remote Access VPN is particularly beneficial for businesses with employees who need to access company resources remotely.
It provides an added layer of security, ensuring that sensitive data remains inaccessible to unauthorized users.
In an era where remote work is increasingly commonplace, the use of VPNs has become integral to maintaining operational security.
Site-to-Site VPN
A Site-to-Site Virtual Private Network (VPN) is an essential tool in modern network architecture, providing a secure connection between two or more local area networks (LANs) over a public network, like the internet.
Primarily, Site-to-Site VPNs are used to bridge geographically separated networks, enabling secure communication between different offices, departments, or branches of a business that are located in different regions.
The fundamental principle of a Site-to-Site VPN lies in its capacity to create a “tunnel” through the public network.
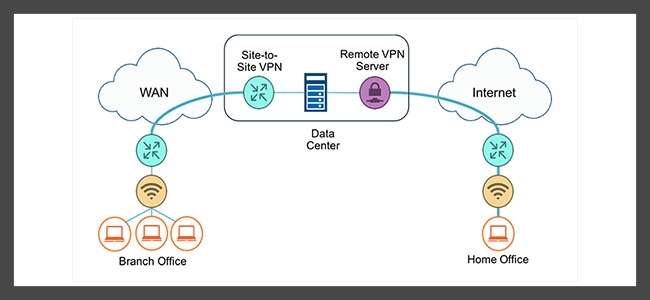
This tunnel protects the data being transmitted from one site to another, ensuring confidentiality and integrity of data against potential interceptions and breaches.
In a sense, a Site-to-Site VPN extends a private network across public infrastructure, allowing secure inter-site communication as if all sites were on the same local network.
Unlike traditional VPNs that are designed for end-user remote access, a Site-to-Site VPN is established between routers or VPN gateways.
These gateways are responsible for encrypting and decrypting data from each site, as well as establishing and managing VPN connections.

Thus, end-users at each site can communicate securely without needing to do anything different or having to install specialized software.
In today’s business landscape where remote work and digital collaboration have become the norm, the relevance and importance of Site-to-Site VPNs cannot be overstated.
They offer a cost-effective solution to connect multiple networks securely, promote seamless inter-site collaboration, and support business continuity in the face of evolving cyber threats.
Therefore, understanding and implementing Site-to-Site VPNs is crucial for organizations aiming to optimize their network infrastructure and maintain robust security measures in an increasingly connected world.
Personal VPN
A Personal Virtual Private Network (VPN) is a private network that creates a secure connection over a public network such as the Internet, safeguarding a user’s internet connection from various online threats.
It provides an encrypted tunnel for your data, protecting sensitive information from being intercepted or accessed by unauthorized individuals.
This makes a VPN essential for preserving privacy and maintaining online security, particularly when using public Wi-Fi networks.
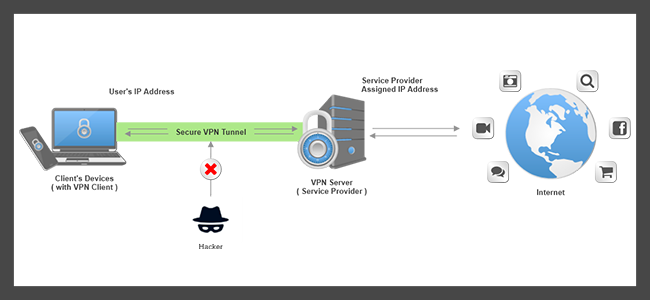
The primary function of a Personal VPN is to hide the user’s IP address and replace it with one from the VPN provider.
This makes it appear as though the user is browsing from a different location, making it harder for third parties to track their online activities.
A Personal VPN also encrypts the user’s data, making it unreadable to anyone who might intercept it.

In addition to its security features, a Personal VPN can also bypass internet censorship and geo-restrictions.
This allows users to access content that may be blocked in their region, enhancing their online freedom.
Furthermore, by masking the user’s original IP address, a Personal VPN helps prevent Internet Service Providers (ISPs) from throttling bandwidth based on usage.
What is a VPN Tunnel and How Does it Work?
A VPN tunnel is a secure, encrypted connection between your device and the internet. It acts as a protective conduit, allowing you to transmit data privately over public or shared networks.
The VPN (Virtual Private Network) tunnel is the virtual version of a secure physical network connection.
The working of a VPN tunnel is crucial to understanding the privacy and security it offers. When you connect to a VPN, your internet traffic flows from your device, through the VPN tunnel, to the VPN server.
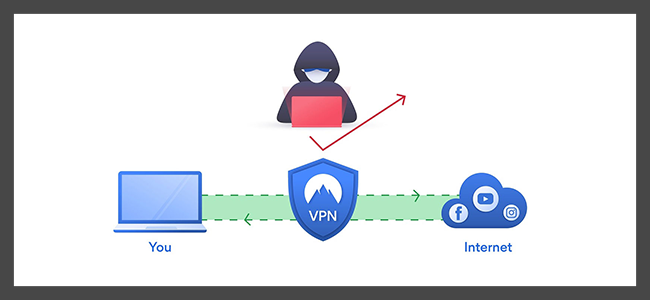
The data you send or receive through this tunnel is encrypted, which means it is converted into a code that only your device and the VPN server can decipher.
This secure data transmission prevents unauthorized entities from intercepting or reading your data.
The VPN tunnel is established using various tunneling protocols such as Layer 2 Tunnel Protocol (L2TP), Point-to-Point Tunneling Protocol (PPTP), Secure Socket Tunneling Protocol (SSTP), or Internet Protocol Security (IPSec).
These protocols create the ‘tunnel’ and also provide the encryption that keeps the data secure.

In essence, a VPN tunnel serves as a protective shield for your internet activity. It hides not only your data but also your IP address, which can reveal your geographical location and other personal information.
By utilizing a VPN tunnel, you’re ensuring the privacy and security of your online activities against potential threats such as cybercriminals, hackers, and even intrusive surveillance by ISPs or governments.
In our increasingly connected world, where data breaches and privacy concerns are escalating, using a VPN and its tunneling capabilities can provide an essential layer of security, helping to safeguard your online presence.
Understanding VPN Encryption
VPN Encryption is an integral aspect of Virtual Private Network (VPN) technology that contributes significantly to safeguarding the security and integrity of data transmitted over a network.
It is a systematic process where data is encoded or converted into an unreadable format, which can only be deciphered by an authorized entity possessing the correct encryption key.
This process is paramount in securing sensitive information, making it difficult for unauthorized individuals or systems to interpret or misuse the data.
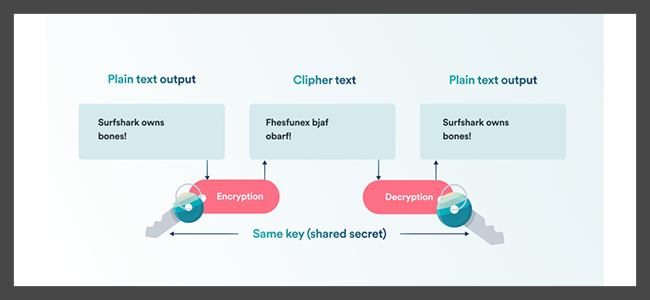
Understanding the concept of VPN Encryption requires a focus on its key components – the encryption algorithm and the encryption keys.
The encryption algorithm is a set of mathematical operations that transforms plain, readable data into cipher text, or encrypted data.
The strength of this encryption is determined by the complexity of the algorithm and the length of the encryption key.

On the other hand, encryption keys are secret codes that are used in combination with the algorithm to encrypt and decrypt the information.
In a VPN context, when a user connects to a VPN server, all their Internet traffic is encrypted using a specific encryption protocol.
This encrypted connection, often referred to as a VPN tunnel, ensures that all data passing through it remains confidential and secure from potential cyber threats.
VPN Protocols
VPN protocols are the methods by which your device connects to a VPN server. Simply put, they are the set of instructions that determine how data is transmitted over a VPN connection.
Each VPN protocol offers a different mix of speed, security, and reliability. These protocols play a crucial role in providing the necessary security and privacy that users require when they connect to the internet via a VPN.

The most common VPN protocols are OpenVPN, PPTP, L2TP/IPSec, IKEv2/IPSec, and SSTP. OpenVPN is one of the most popular and recommended due to its strong security and high performance.
PPTP, while much older and less secure than other protocols, is still used due to its speed.
L2TP/IPSec is a combination of the L2TP and IPSec protocols, offering robust security but sometimes at the expense of speed.

IKEv2/IPSec is a modern protocol that offers both solid security and fast connections, particularly on mobile devices.
Lastly, SSTP is fully integrated with Microsoft operating systems and offers strong encryption but lacks some of the flexibility of other protocols.
How Do VPN Servers Work?
At its core, a VPN works by establishing a secure, encrypted connection between your device and a server located elsewhere.
This process, often termed as ‘tunneling’, involves encapsulating the data sent and received within secure VPN protocols.
It masks your IP address, making it appear as though your device is accessing the internet from the location of the VPN server rather than your actual location.
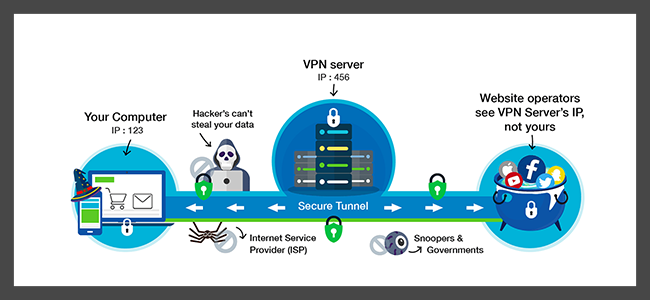
This not only safeguards your identity but also enables you to bypass geo-restrictions on content.
There are several different VPN protocols that dictate how data is handled. Some of these include OpenVPN, IPsec, and WireGuard. Each protocol has its strengths and weaknesses in terms of security, speed, and compatibility.
The choice of protocol depends on the user’s specific requirements and the nature of the data being transmitted.

Users connect to VPN servers using VPN client software. This software takes care of initiating the connection, encrypting data, and maintaining the connection throughout the session.
Once connected, all web traffic passes through this encrypted tunnel, ensuring that the data remains inaccessible to prying eyes.
In essence, VPN servers act as intermediaries between your device and the internet. They provide an additional layer of security by disguising your actual IP address and encrypting your data.
As such, understanding how VPN servers work is crucial for anyone concerned about maintaining their digital privacy.
Choosing the Right VPN
When it comes to choosing a VPN, consider factors like speed, security, and privacy.
While most VPNs offer secure connections and hide your IP address, not all provide high-speed connections or restrict the logging of your activities.
Therefore, make sure to choose a reliable VPN provider that offers a balanced mix of speed, security, and privacy.
Paid VPNs Vs. Free VPNs
The debate between utilizing Paid VPNs and Free VPNs has been ongoing, with both having their own advantages and drawbacks.
Paid VPN services tend to excel in terms of performance, reliability, and security. They typically have a larger number of servers across various geographical locations, providing faster speeds and a wider range of IP addresses.
Most importantly, they prioritize user privacy, often implementing robust encryption protocols and no-logs policies. Paid VPNs also offer superior customer support and additional features such as kill switches and simultaneous connections on multiple devices.
They provide a professional level of service, ensuring that your data is secure and your connections are stable.
On the other hand, Free VPNs have their own set of benefits. They are a cost-effective solution for users who require basic VPN functionality for casual browsing or accessing geo-restricted content.

However, they often come with limitations such as data caps, slower speeds due to overcrowded servers, and fewer server locations.
A significant concern with Free VPNs is the potential compromise on privacy. Some free services sustain their operations by selling user data to third parties or displaying advertisements.
The 5 Most Popular VPN Service Providers
In the following section, we will provide an in-depth look into the 5 most popular VPN service providers currently dominating the market.
These platforms have been selected based on their performance, security measures, user-friendly interfaces, and overall customer satisfaction.
By understanding the unique features of these popular VPN providers, you can make an informed decision that best suits your online needs and ensures your digital footprint remains protected.
NordVPN
Pros
- High-grade encryption technology for enhanced security.
- A vast network of servers worldwide for better access and bypassing geo-restrictions.
- CyberSec feature for ad blocking and additional malware protection.
- Allows up to six simultaneous connections.
Cons
- Inconsistent connection speed across different servers.
- Connecting multiple devices can sometimes be challenging.
NordVPN stands as one of the most popular VPN services in the world, admired for its robust security features, easy-to-use interface, and excellent customer service.
One of the defining features that make NordVPN so popular is its ability to provide top-tier encryption technology.
It uses advanced encryption standard (AES) with 256-bit keys, which is typically referred to as military-grade encryption. This ensures that users’ data remains secure while surfing the web.
Another feature that contributes to the popularity of NordVPN is its vast network of servers.

With over 5000 servers in 59 countries, users have a wealth of options for masking their IP addresses and bypassing geo-restrictions.
Furthermore, NordVPN offers a feature called CyberSec, which provides ad blocking and extra malware protection.
However, like any product or service, NordVPN also has its drawbacks. The speed of connection can sometimes be inconsistent, with some servers offering fast speeds while others lag behind.
Additionally, although NordVPN allows up to six simultaneous connections, users have reported that connecting multiple devices can sometimes be a challenging process.
Surfshark
Pros
- High-speed connections.
- Unlimited simultaneous connections.
- Supports a wide range of platforms.
- Robust security features.
- No-logs policy.
- Kill switch feature.
- Bypasses geographical restrictions.
Cons
- Slower speeds on distant servers.
- Customer support can be slow.
- Lacks some advanced features like split tunneling on all platforms.
Surfshark, a popular VPN, has built a strong reputation within the industry due to its unique features and robust service offerings.
It offers high-speed connections and unlimited simultaneous connections, making it stand out from its competitors.
Surfshark supports a wide range of platforms, including Windows, MacOS, Linux, Android, and iOS. Additionally, it offers browser extensions for Chrome and Firefox.
The VPN also boasts of a robust security feature with AES-256-GCM encryption and supports OpenVPN and IKEv2/IPsec protocols.

Surfshark’s no-logs policy ensures that users’ online activities are not tracked or stored. The VPN service also offers a kill switch feature, which automatically disconnects the user’s internet connection if their connection to the VPN drops unexpectedly.
This prevents data leakage and maintains the user’s privacy. Another popular feature of Surfshark is its ability to bypass geographical restrictions, allowing users to access content from anywhere in the world.
Despite these advantages, Surfshark does have a few disadvantages. Some users have reported slower speeds when using the VPN service, particularly on distant servers.
The company’s customer support has also been criticized for sluggish responses. The VPN lacks some advanced features offered by competitors, such as split tunneling on all platforms.
CyberGhost
Pros
- Robust security and privacy features.
- Extensive server network.
- Intuitive user interface.
- Supports multiple simultaneous connections.
Cons
- Inconsistent speeds across different servers.
- May not work in highly censored countries.
- No free version available.
CyberGhost, a popular Virtual Private Network (VPN) service provider, has won the hearts of many users worldwide due to its top-notch features and performance.
The benefits offered by CyberGhost are multifaceted and cater to a diverse range of users, from casual internet surfers to tech-savvy professionals.
One of the significant advantages of CyberGhost is its robust security and privacy features. With advanced encryption standards, CyberGhost ensures that users’ connections are secure and their data remains private.
This VPN also operates a strict no-logs policy, meaning they do not keep any records of user activity, further ensuring privacy.
CyberGhost’s extensive server network is another feature that makes it a popular choice. With over 7,000 servers in almost 90 countries, it provides users with a broad range of options for server location.
This vast network also ensures excellent speed and performance, making it ideal for high-bandwidth activities like streaming and gaming.
User experience is also enhanced with CyberGhost’s intuitive interface, which is easy to navigate even for novice users.
Additionally, the VPN supports simultaneous connections on up to seven devices, offering versatility for users with multiple devices.
However, there are a few potential downsides to CyberGhost. While it generally offers fast speeds, some users have reported inconsistent performance across different servers.
Also, despite having a broad server network, it may not work in countries with stringent internet censorship policies like China.
Lastly, although CyberGhost’s pricing is competitive, there is no free version available which may deter some potential users.
Private Internet Access
Pros
- Strict no-logs policy ensures user privacy.
- High standard encryption methods for data security.
- Wide server network bypasses geo-restrictions effectively.
- Supports simultaneous connections on up to 10 devices.
Cons
- Connection speeds can be inconsistent.
- Customer service can be slow and unresponsive.
Private Internet Access (PIA) is one of the most popular VPNs for a variety of reasons. It offers a plethora of features that contribute to its popularity among users worldwide.
One of the standout features of PIA is its strong commitment to privacy. It has a strict no-logs policy, meaning it does not collect or keep any activity logs from its users.
This means that even if authorities were to request information, PIA would have nothing to hand over, thus ensuring user privacy.
Moreover, PIA uses high-standard encryption methods, ensuring that your data is secure and protected from prying eyes.
PIA is also known for its wide server network. It has over 3300 servers in 30+ countries, giving users a vast array of options for connection points and making it easier to bypass geo-restrictions.
Furthermore, PIA supports simultaneous connections on up to 10 devices, making it an ideal choice for individuals and families alike.
However, it’s important to consider the potential drawbacks of using Private Internet Access. Some users have reported that the connection speeds can be inconsistent.
While PIA generally provides fast and reliable connections, some servers may lag or disconnect entirely. Additionally, PIA’s customer service has been critiqued for being slow and unresponsive at times.
In conclusion, while Private Internet Access has a few drawbacks, its strong commitment to privacy, robust security features and comprehensive server network make it one of the most popular VPNs in the market today.
ExpressVPN
Pros
- Robust 256-bit encryption for superior security.
- No-logs policy ensures user privacy.
- Wide network of over 3000 servers in 94 countries.
- High-speed connections and low latency.
Cons
- Higher cost compared to other VPNs.
- Allows only up to five simultaneous connections.
ExpressVPN has rapidly ascended the ranks to become one of the most popular Virtual Private Networks (VPNs) available today.
The reasons for its popularity are multifaceted, encompassing a range of features that meet and exceed user expectations.
ExpressVPN provides robust security, deploying 256-bit encryption to protect user data. This level of security is utilised by many governmental and military institutions, which indicates its reliability.
Furthermore, ExpressVPN offers a no-logs policy, ensuring that users’ online activities are not tracked or recorded. This feature is particularly crucial for individuals concerned about their privacy.
Another appealing feature of ExpressVPN is its vast network of servers. With over 3000 servers located in 94 countries, users have a wide array of choices for their virtual locations.
This broad network also enhances the VPN’s performance, providing high-speed connections and reducing latency issues.
Despite these impressive features, ExpressVPN is not without its drawbacks. One of the main disadvantages is the cost.
While ExpressVPN offers premium features, it also comes with a premium price tag, making it one of the more expensive VPNs on the market.
Another potential downside is that it only allows up to five simultaneous connections. For users with multiple devices or larger households, this limitation may prove challenging.
Setting Up a VPN

Here, we provide a step-by-step guide on setting up a VPN.
- Choose a VPN Service: The first step in setting up a VPN involves selecting a VPN service that best fits your needs. When making this decision, consider factors such as cost, speed, privacy policies, and the number of available servers.
- Download and Install the VPN Software: Once you’ve chosen a VPN service, visit their website and download the appropriate software for your device. This could be a desktop computer, laptop, smartphone or tablet. After downloading, install the software following the provided instructions.
- Set Up Your VPN: Open the installed VPN software and sign in using your account details. If you don’t have an account yet, you’ll need to create one.
- Configure Your Settings: Most VPNs will allow you to customize your settings. This can include choosing the server location you want to connect through or adjusting your security protocols.
- Connect to the VPN: Once your settings are configured, you can connect to the VPN. There should be a conspicuous “Connect” button on the software’s interface.
- Verify Your Connection: After connecting, it’s important to verify that your VPN is working correctly. You can do this by checking your IP address online to ensure it’s different from your actual one.
- Maintain Your VPN: Regularly update your VPN software to ensure optimal performance and security.
Summary
In conclusion, a VPN is an essential tool for securing your online activities and ensuring your data’s privacy. Understanding what a VPN is and how it works can help you make the most of this powerful tool.
Whether you’re an individual wanting to safeguard your personal information or a business looking to protect your data, a VPN can be a reliable solution.