In the digital realm, privacy and security are paramount. One tool that has gained popularity for its ability to provide both is the Virtual Private Network (VPN). At the core of a VPN’s functionality is a process known as encryption.
But what exactly is VPN encryption, and how does it work? If you’ve ever asked these questions, this comprehensive guide is for you. We will delve into the intricacies of VPN encryption, its importance, the types of encryption used, and much more.
What is a VPN?
A VPN, or Virtual Private Network, is a service that allows you to connect to the internet in a secure manner. It essentially acts as a secure tunnel between your device and the internet.
When you use a VPN, your online actions are virtually untraceable and vastly more secure, making it an essential tool in maintaining privacy and security in our digital age.
So, what is a VPN exactly? A VPN works by routing your device’s internet connection through the VPN’s private server rather than your internet service provider (ISP).
This process masks your IP address—making it appear as though your physical location is different than what it actually is—and encrypts the data sent and received by your device during an online session. The end result is a safer, more private browsing experience.
VPNs are often used by businesses to protect sensitive data. However, personal usage of VPNs has grown exponentially over the years due to increasing concerns about online privacy and security.
From protecting your personal data from hackers on public Wi-Fi networks to bypassing geo-restrictions and censorship, VPNs offer a wide array of benefits.
What is Encryption?
Encryption is a fundamental aspect of modern data security and privacy. It is a process that encodes information or data in such a way that only authorized parties can access it.
The technique involves the conversion of readable data, known as plaintext, into an unreadable format, referred to as ciphertext, using an algorithm and an encryption key.
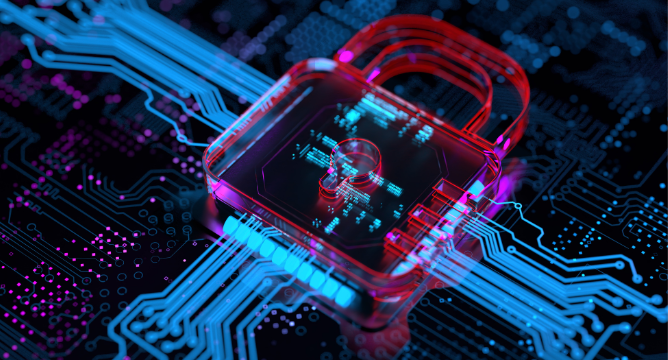
The main purpose of encryption is to protect the confidentiality of digital data stored on computer systems or transmitted via the internet or other networks.
The concept of encryption is not new, with its roots tracing back to ancient times when secret messages were written in code to prevent unauthorized reading.
However, in the digital age, encryption has become more sophisticated and essential due to the increasing volume of sensitive information shared online.

One common use of encryption today is in creating secure connections over the internet through Virtual Private Networks (VPN).
VPN Encryption ensures that data traveling over a VPN is unreadable to any unauthorized individual who might intercept it.
This makes it an essential tool for protecting sensitive data like personal information, emails, and financial transactions.
VPN vs Encryption: Understanding the Difference
Encryption is a method of converting data into an unreadable format, or cipher text, to prevent unauthorized access. It uses algorithms and mathematical computations to scramble data into unreadable text which can only be read or decrypted by someone who possesses the correct encryption key.
The primary purpose of encryption is to protect the confidentiality of digital data stored on computer systems or transmitted via the internet or other computer networks.

On the other hand, a Virtual Private Network (VPN) is a technology that creates a secure, encrypted connection over a less secure network, such as the public internet.
A VPN uses encryption to ensure that data transmitted between your device and the VPN server is not intercepted by others. In essence, it provides a protective shield to your online activities from prying eyes on public networks.
When comparing VPN vs Encryption, it’s important to understand that these two technologies serve different yet overlapping purposes.

VPNs use encryption as a tool within their service, but they also provide additional benefits such as masking your IP address and location.
On the contrary, encryption as a standalone does not hide your IP address or location, but it ensures the data, be it in transit or at rest, is secure from unauthorized access.
Encryption Methods Employed by VPNs
VPNs utilize different encryption methods to secure your data. Here are some commonly used methods:
Symmetric Encryption
Symmetric encryption, also known as private-key cryptography, is a type of encryption where the same key is used for both the encryption and the decryption of the data.
This signifies that the sender and the receiver must share the same key, which is kept secret. The primary advantage of symmetric encryption lies in its simplicity and speed; as it uses less computational power, it can be faster and more efficient than other types of encryption methods.
The process of symmetric encryption begins when a user enters plaintext information into an encryption software. The software then generates a secret key, which is used to convert the plaintext into an unreadable form known as ciphertext.
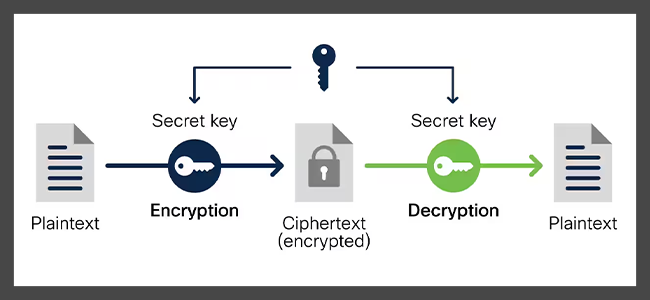
This conversion process is performed by an algorithm that creates a unique relationship between the plaintext and the key, making it virtually impossible to decipher without the correct key.
When the encrypted data needs to be read, the same key is used for decryption. The decryption software applies this key to the ciphertext, reversing the algorithm and converting back into readable plaintext.
Without the correct key, the decryption process cannot occur, thus ensuring the security of the information.
One potential risk associated with symmetric encryption is key distribution. Both parties must have access to the same key without it being intercepted by unauthorized individuals.
If an unauthorized party were to gain access to this key, they would be able to decrypt any information encrypted with it. Therefore, secure methods of key exchange are paramount for maintaining the integrity of symmetric encryption.
AES Encryption
AES Encryption, also known as Advanced Encryption Standard, is a symmetric encryption algorithm established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
This encryption standard is widely recognized across the globe and is utilized by the US government for encrypting classified information, thereby affirming its high level of security.
AES Encryption works by using the same key for both encryption and decryption processes. The algorithm applies multiple rounds of transformations to the plain text data blocks to generate the cipher text.
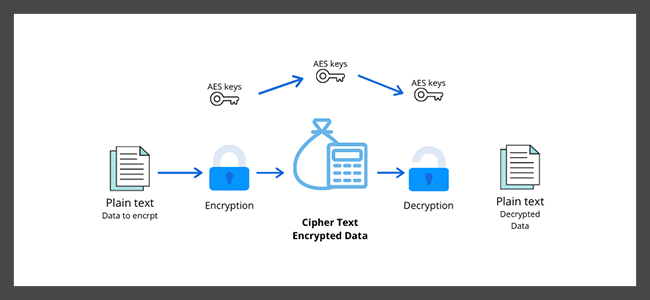
These transformations include substitution, permutation, mixing, and a round key addition. The number of rounds depends on the key size, with 10 rounds for a 128-bit key, 12 rounds for a 192-bit key, and 14 rounds for a 256-bit key.
To further elucidate, in the substitution step, each byte in the block is replaced by another byte from a lookup table. Permutation rearranges the bytes to mix the data.
The mixing step further confuses the relationship between key and ciphertext by mixing data within each column. Lastly, in round key addition, a round key derived from the original AES key is added to each byte.
Public-key Encryption
Public-key encryption, also known as asymmetric encryption, is a fundamental concept in the field of cryptography used extensively to secure sensitive data transmission over an unsecured network.
It forms the backbone of several data security practices and protocols, including SSL and TLS. The uniqueness of public-key encryption lies in its two-key cryptographic system, which involves a pair of keys—a public key and a private key.
The public key, as the name suggests, is distributed publicly for anyone to use, while the private key remains confidential with the owner.
The mechanism of public-key encryption is rather ingenious. For instance, if a sender wants to send an encrypted message to a receiver, they would encrypt their message using the receiver’s public key.
This encrypted message can now safely be transmitted over an unsecured network without fear of it being deciphered if intercepted.
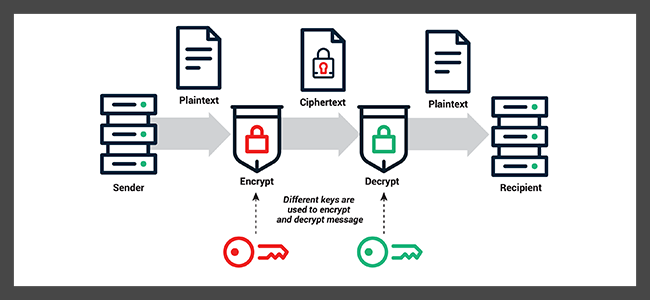
However, once the receiver gets the encrypted message, only their private key can decrypt it to reveal the original message. This is because the public and private keys are mathematically linked—what one key encrypts, only the other can decrypt.
The public-key encryption system not only ensures confidentiality of information but also provides a method for digital signatures which can verify the authenticity and integrity of a message.
If the sender encrypts a message with their private key, anyone can decrypt it with the sender’s public key—validating that the decrypted message has indeed been sent by the sender and has not been tampered with during transit.
In essence, public-key encryption provides an incredibly robust and versatile framework for maintaining digital security. It’s a critical component in modern information technology systems, protecting data integrity and confidentiality while ensuring reliable authentication.
Transport Layer Security (TLS)
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network.
It is the most widely deployed security protocol used today and is extensively used to secure various types of communications across the Internet, including web browsing, email, instant messaging, and voice-over IP (VoIP).
The primary goal of TLS is to provide privacy and data integrity between two communicating applications.
The operation of Transport Layer Security (TLS) involves a series of steps. Initially, it starts with a handshake between the sender and receiver to establish a secure connection.
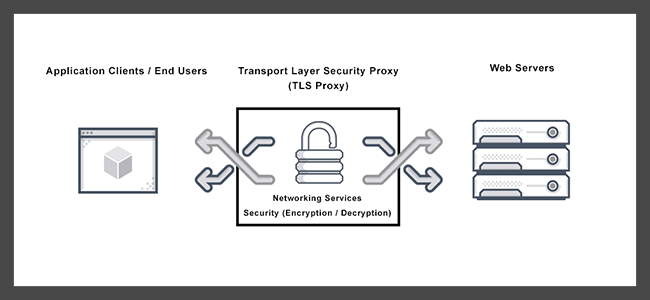
During this handshake, both parties agree on various parameters to establish the connection’s security settings.
They will authenticate each other, select cryptographic algorithms, exchange random values used in the encryption process, and agree on a session key.
Following the handshake, the sender uses the agreed-upon encryption algorithm and session key to convert plaintext data into an encrypted format (cipher-text).
This encrypted data is then sent over the network. The receiver, upon receiving the cipher-text, uses the same session key to decrypt it back into the original plain text.
TLS utilizes asymmetric cryptography for authentication and key exchange during the establishment of a connection and symmetric encryption for maintaining privacy during the data transfer phase.
This combination provides a robust framework of security measures that help protect data from threats such as eavesdropping, tampering, or message forgery.
VPN Encryption and Your IP Address
VPN encryption is a technique that creates a secure tunnel for your data to travel over the internet, keeping it away from prying eyes and cybercriminals.
This mechanism works by encrypting or converting your data into an unreadable format when it leaves your device until it reaches its intended destination, where it is then decrypted back into its original form.

A significant part of this process involves your Internet Protocol (IP) address. An IP address is a unique set of numbers and decimals that identifies your device and enables communication between different devices over the internet.
When you are not using a VPN, your IP address is visible to others, which can expose your location and sensitive information to potential threats.

However, a VPN masks your actual IP address. When you connect to a VPN server, your original IP address is replaced with one from the VPN server.
This not only keeps your online activities private but also makes it appear as though you’re browsing from the server’s location – effectively disguising your actual location. Consequently, this aids in preventing websites and online services from tracking and profiling your online behavior.
Importance of VPN Encryption
The role of VPN Encryption in preserving online security cannot be overstated. When data is transmitted over the internet, it is vulnerable to interception by malicious parties.
This could lead to identity theft, financial loss, or even corporate espionage. VPN encryption effectively eliminates this risk by encoding the transmitted data so that it can only be decoded by the intended recipient.
This encoding is done using complex algorithms that are nearly impossible to break, making the data useless to anyone who intercepts it.
Moreover, VPN encryption also provides privacy by masking the user’s IP address. This prevents websites and online services from tracking a user’s activity or determining their physical location.
This feature is particularly beneficial for individuals living in regions where internet access is heavily censored or monitored.
Choosing the Most Secure VPN
When choosing a VPN, look for one with a trusted encryption method and secure VPN protocol. Consider features like split tunneling, multi-hop technology, streaming support, torrenting support, kill switch, and a clear privacy policy. Also, consider the VPN’s location, encryption tools, protocols, speeds, and price.
Remember, the most secure VPNs typically use AES-256 encryption and have a no-logs policy, meaning they don’t keep track of your online activities.
FAQs
VPNs, or Virtual Private Networks, are generally safe to use. They provide a secure and encrypted tunnel for your data to travel through, protecting your personal information from potential threats such as hackers and cybercriminals. They also mask your IP address, making it difficult for third parties to track your online activities.
However, not all VPNs are created equal. Some may not provide adequate levels of security and privacy. For example, free or low-cost VPNs may lack robust encryption protocols, making your data more susceptible to breaches. Additionally, some VPNs may log your data and sell it to third parties, which compromises your privacy.
Another factor to consider is the legal and regulatory environment in your country. In some jurisdictions, the use of VPNs is heavily regulated, or even prohibited. It’s crucial to understand these laws before using a VPN.
There’s also the question of trust. When you use a VPN, all your online traffic passes through the VPN provider’s servers. Therefore, you must trust that the provider will respect your privacy and not misuse your data.
Remember, using a VPN is only one part of online safety. You should also use strong, unique passwords for your accounts, enable two-factor authentication where possible, and maintain up-to-date antivirus software on your devices.
Can a VPN Be Traced?
A Virtual Private Network (VPN) is essentially a set of servers that you connect to through your internet service provider (ISP). The connection between your device and the VPN server is securely encrypted, which increases online privacy and prevents your ISP, hackers, or eavesdroppers from viewing your online activities. However, the question arises, can a VPN be traced?
Technically, it is challenging, but not impossible, to trace someone using a VPN. Here’s why:
- VPN Provider Logs: Some VPN providers may keep logs of your internet activity, including your IP address, the websites you visit, and any data you download or upload. If these logs are accessed or subpoenaed by authorities, your VPN usage could theoretically be traced. Therefore, if privacy is a concern, opt for a VPN provider that adheres to a strict no-logs policy.
- IP Leaks: If your VPN connection drops suddenly, your original IP address could be exposed briefly. Some VPNs offer an automatic kill switch feature that halts all internet traffic when the VPN connection is lost, reducing the risk of IP leaks.
- DNS Leaks: When you access a website, a DNS request is sent to translate the domain name to an IP address. If these requests are being sent outside of the secure VPN tunnel, it can reveal your online activity to your ISP, a situation known as a DNS leak.
- Advanced Tracking Techniques: Certain organizations, like government agencies, may use advanced tracking techniques that can potentially trace VPN activity. However, these techniques are generally not used for routine surveillance due to their technical complexity and cost.
For example, if an individual were using a VPN to post anonymously on a forum, tracing their activity would be difficult for the average person. However, if a government agency were investigating a serious crime, they might be able to trace the VPN activity by correlating activity logs from various sources.
In summary, while a VPN significantly enhances your online privacy and security, it doesn’t render you completely anonymous or untraceable. It’s always advisable to follow good internet practices, like not sharing sensitive information online, even when using a VPN.
Are Free VPNs Any Good?
Free Virtual Private Networks (VPNs) are a tempting proposition for users looking to maintain their privacy online. However, their use comes with several key considerations that can influence their overall effectiveness and safety.
The primary function of a VPN is to establish a secure connection to another network over the internet. This secure connection provides a layer of anonymity by masking your IP address, thereby making your online activities more private. It’s also used to access region-restricted websites by making it appear as though you’re browsing from another location.
Many free VPNs do accomplish this basic function. However, the quality, safety, and reliability often fall short when compared to their paid counterparts. Here’s why:
- Limited Data and Speed: Free VPNs often impose data limits and slower connection speeds which can hinder your browsing experience. For instance, you might only be allowed to use 500MB of data per month, or the speed may be throttled during peak usage times.
- Privacy Concerns: Free VPNs need to make money to support their service. Some do this by tracking your online activities and selling this information to third parties. This completely undermines the purpose of a VPN in protecting your privacy.
- Limited Security: Free VPNs may not invest in the high-end encryption protocols that paid services do, putting your data at risk.
- Limited Server Options: Most free VPNs have limited server options. This means you might not be able to connect to your desired location.
- Ads and Pop-ups: To support their free offering, many free VPNs include numerous ads and pop-ups in their service which can be annoying and disruptive.
For example, a popular free VPN, Hola VPN, faced criticism for selling users’ bandwidth. Another free service, Betternet VPN, was found to be injecting ads and tracking cookies into users’ browsers.
Ultimately, while free VPNs can provide some level of anonymity and access to geo-restricted content, their potential drawbacks and risks make them less than ideal. If privacy, security, and reliable performance are your main concerns, it would be worth investing in a reputable paid VPN service.
Is VPN Encryption Secure?
Yes, VPN encryption is secure, and it is one of the main reasons why people use a Virtual Private Network (VPN). A VPN encrypts, or scrambles, data so that it can’t be intercepted by others, making it secure for use even on unsecured public Wi-Fi networks.
The level of security VPN encryption provides, however, depends on the type of encryption protocol used. Some of the most commonly used encryption protocols in VPNs are OpenVPN, L2TP/IPSec, and IKEv2/IPSec.
OpenVPN, for instance, uses a 256-bit encryption key, which is currently considered the industry standard. To put it in perspective, a hacker attempting to crack a 256-bit key using a brute-force attack (guessing all possible combinations) with a supercomputer would need billions of years to succeed, making it practically impossible.
L2TP/IPSec and IKEv2/IPSec are also secure protocols, offering similar encryption levels. However, they may not be as fast or as flexible as OpenVPN.
It’s important to mention that while VPN encryption is secure, it doesn’t mean that using a VPN makes you completely anonymous or immune to all threats.
VPNs are a tool in your security toolkit and should be used as part of a broader approach to online security, including strong passwords, two-factor authentication, secure Wi-Fi connections, and updated software.
So, while VPN encryption provides a robust layer of security for your data, it’s still crucial to be mindful of additional security practices to ensure complete online safety.
Conclusion
In the current digital landscape where data privacy and security breaches are rampant, VPN encryption serves as a vital defense line.
It masks your online activities, protects your sensitive information, and offers you the freedom to access the internet without fear of being tracked or monitored.
However, remember that while a VPN significantly enhances your online security, it’s not a silver bullet for all cyber threats.
Always complement it with robust antivirus software and safe online practices for comprehensive protection.





