Public Key Encryption, a major cornerstone in the realm of digital security, is a mechanism that safeguards information through the use of two interlinked cryptographic keys. The concept of Public Key Encryption is intriguing and complex, yet its application is fundamental to our everyday digital interactions.
What is Public Key Encryption: An Overview

At its core, Public Key Encryption, often termed as asymmetric cryptography, is a method of encrypting data that uses a pair of keys: a public key and a private key. These keys, despite being distinct, are mathematically intertwined. While the public key is made accessible to everyone, the private key remains confidential with its owner.
Note: The public key is used to encrypt data, and the corresponding private key decrypts it.
This unique system of encryption locks up data from unauthorized access, making our digital communications secure and private.
Origin of Public Key Encryption
The inception of Public Key Encryption dates back to 1976 when Whitfield Diffie, Martin Hellman, and Ralph Merkle published a paper titled “New Directions in Cryptography“. This revolutionary paper introduced the world to the concept of public key cryptography, laying the foundation of modern digital security.
How Does Public Key Encryption Work?
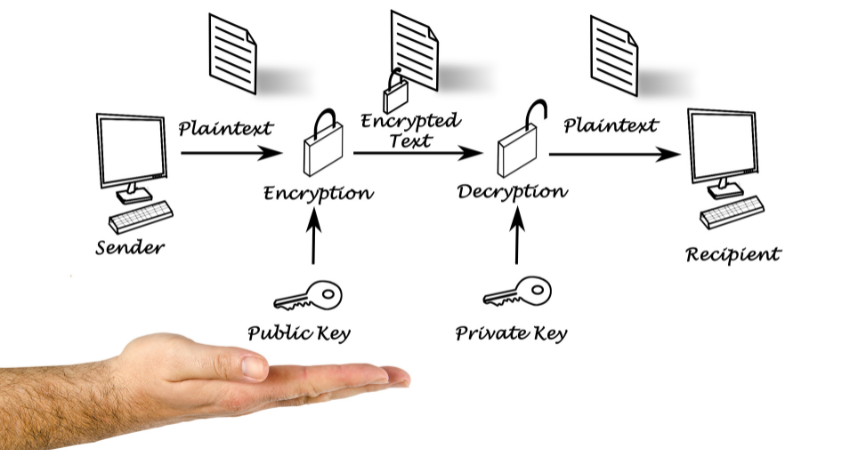
Understanding how Public Key Encryption works is pivotal to comprehending its significance. The process can be broken down into the following steps:
- Key Generation: Individuals generate their public and private key pair.
- Key Exchange: The public keys are exchanged between the sender and the recipient.
- Encryption: Data is encrypted using the recipient’s public key.
- Transmission of Encrypted Data: The encrypted data is sent to the recipient.
- Decryption: The recipient uses their private key to decrypt the message.
The use of two keys in this process ensures the secure transmission of data, with the private key serving as the unique decoder of the encrypted messages.
Main Applications of Public Key Encryption

Public Key Encryption finds its utility in a variety of applications, some significant ones being:
- Encryption: The foremost use of Public Key Encryption is to secure data transmission. The recipient’s public key is used to encrypt data, and the unique corresponding private key is used for decryption.
- Digital Signatures: Public Key Encryption facilitates the creation of digital signatures, ensuring the authenticity of digital documents.
- Secure Socket Layer (SSL) and Transport Layer Security (TLS) connections: SSL/TLS employ public key encryption to establish secure connections between servers and clients.
Risks Associated With Public Key Encryption
Despite the security advantages, Public Key Encryption does come with certain risks.
- Low-quality Key: A poorly designed asymmetric key can become a potential security risk.
- Lost Private Key: Misplacement or loss of the private key can lead to data access issues.
- Man-in-the-middle (MitM) Attacks: Public Key Encryption can become a target for MitM attacks.
Conclusion
Understanding what Public Key Encryption is and how it works is not just essential for IT professionals but for anyone using digital platforms. As we continue to embrace digital transformation at an unprecedented pace, the importance of encryption and data security will only continue to grow.





