In the world of data protection, symmetric encryption reigns as a cost-effective solution. But what is symmetric encryption exactly? This article provides a thorough understanding of the concept, its workings, and applications.
Defining Symmetric Encryption
Symmetric encryption, also known as symmetric cryptography, is a method of data protection involving a secret key for both encrypting and decrypting data.
The key can be anything from a word, a phrase, or a random string of characters, numbers, and symbols. It’s like a combination lock, where anyone with the combination can unlock and access the contents.
Why Use Symmetric Encryption?
Symmetric encryption is a popular choice for many organizations due to its relative cost-effectiveness. However, it is not without its shortcomings.
For example, the encryption key can be used indefinitely, leading some organizations to forget to change them. This could potentially allow unauthorized users to intercept and decrypt the data.
Exploring Symmetric Encryption Algorithms

Symmetric encryption utilizes various algorithms to transform data into a form that only those with the secret key can understand. Here are some commonly used symmetric encryption algorithms:
Data Encryption Standard
The Data Encryption Standard (DES) was once the standardized method for encrypting electronic communications, but it was soon deemed weak and unable to cater to the high processing power requirements of modern computers.
Advanced Encryption Standard
The Advanced Encryption Standard (AES) is one of the most popular symmetric encryption algorithms. It’s set as the standard for encrypting electronic data by the National Institute of Standards and Technology (NIST).
International Data Encryption Algorithm
The International Data Encryption Algorithm (IDEA) is widely used to secure large data sets divided into chunks.
Other symmetric encryption algorithms include Blowfish, Rivest Cipher 4 (RC4), Rivest Cipher 5 (RC5), and Rivest Cipher 6 (RC6).
How Symmetric Encryption Works
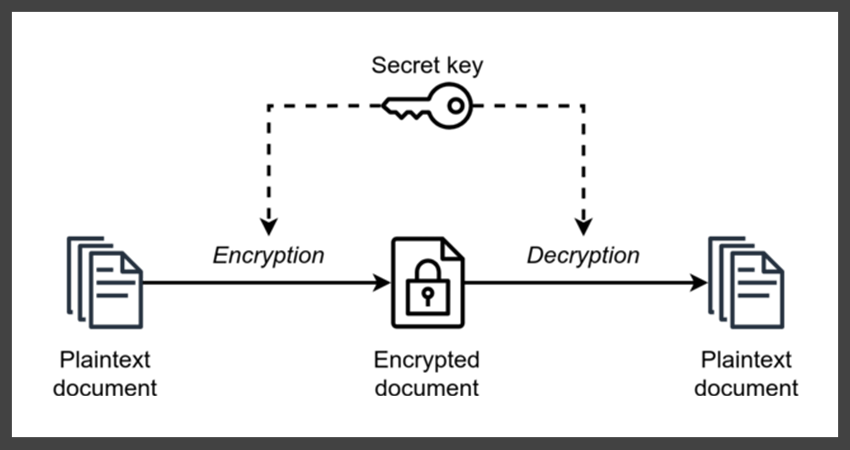
Symmetric encryption works similarly to a locked door, where only the holders of the key can open it. In this case, the key that encrypts a message or file is the same key that can decrypt them.
Uses of Symmetric Encryption

Despite being an older form of data security, symmetric encryption is still widely used due to its ease of deployment and better performance compared to asymmetric encryption. It plays an integral role in website security, specifically in how HTTPS works.
Several messaging applications, such as Telegram, Line, and KakaoTalk, also use symmetric encryption, particularly the AES algorithm.
Other use cases of symmetric encryption include managing cloud storage security, preventing fraud in payment applications and card transactions, validating the identity of a message sender, and generating random numbers or hashing.
Drawbacks of Symmetric Encryption

Like any other system, symmetric encryption has its flaws:
Prone to Key Leakage
Symmetric encryption can be relatively easy to hack. Once part of the key is leaked, hackers can reconstruct the entire key and access confidential data.
Lack of Attribution Data
Symmetric encryption does not allow users to record information in an access control list or monitor usage based on expiration dates.
No Management System
When used on a large scale, manually tracking secret keys can become impractical, especially for transactions involving significant amounts of sensitive information.
In conclusion, symmetric encryption is a critical method for securing sensitive data. Its challenges, however, need to be addressed, especially in financial and banking institutions where security and audibility are paramount.
Table: Comparison of Symmetric Encryption Algorithms
| Algorithm | Pros | Cons |
|---|---|---|
| DES | Standardized method | Found weak and insufficient |
| AES | Most popular, set as standard | Requires high processing power |
| IDEA | Secures large data sets | Not commonly used |
Remember: The key to understanding symmetric encryption lies in its simplicity and efficiency. Despite its drawbacks, it remains a crucial part of our digital security infrastructure.