SSH Tunnels, often referred to as SSH port forwarding, are a powerful tool for transmitting arbitrary networking data over a secure SSH connection. They can bolster the security of legacy applications, implement VPNs, and facilitate access to intranet services from across firewalls.
What is an SSH Tunnel?
SSH Tunneling, simply put, is a method of transporting arbitrary networking data over an encrypted SSH connection. It is a standard for secure remote logins and file transfers over untrusted networks.
It also provides a way to secure the data traffic of any given application using port forwarding, basically tunneling any TCP/IP port over SSH.
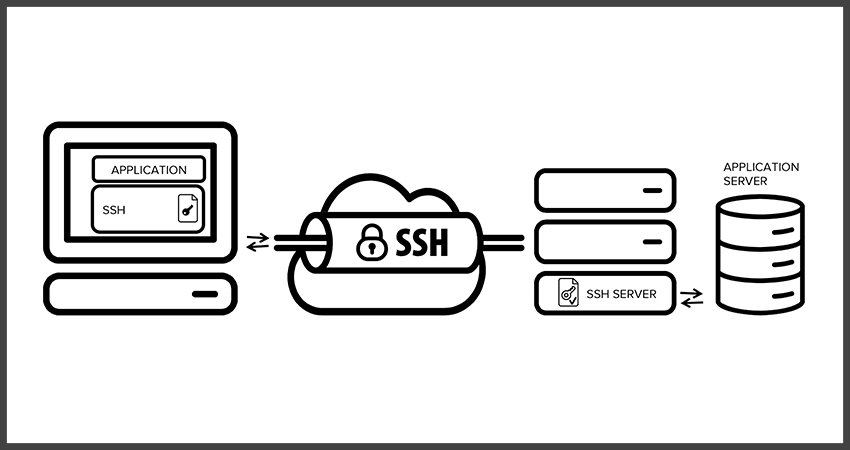
This figure presents a simplified overview of SSH tunneling. The secure connection over the untrusted network is established between an SSH client and an SSH server.
The SSH connection is encrypted, protects confidentiality and integrity, and authenticates communicating parties.
Who Uses SSH Tunneling?

SSH tunnels are extensively used in corporate environments that employ mainframe systems as their application backends. In these environments, the applications themselves may have very limited native support for security.
By utilizing tunneling, compliance with SOX, HIPAA, PCI-DSS, and other standards can be achieved without having to modify applications.
# Example of SSH Tunnel Use
ssh -L 8080:localhost:80 external-hostHowever, SSH tunneling can also be exploited maliciously. Hackers and malware can use it to leave a backdoor into the internal network. It can also be used for hiding attackers’ tracks by bouncing an attack through multiple devices that permit uncontrolled tunneling.
SSH Tunneling in the Corporate Risk Portfolio
Despite the benefits, SSH tunneling also poses risks that need to be addressed by corporate IT security teams.
SSH connections are protected with strong encryption, rendering their content invisible to most deployed network monitoring and traffic filtering solutions.

This invisibility carries considerable risk potential if it is used for malicious purposes such as data exfiltration.
Cybercriminals or malware could exploit SSH tunnels to hide their unauthorized communications, or to exfiltrate stolen data from the target network.
SSH tunneling attacks can also be used for hiding the source of the attack by bouncing attacks off systems and devices that allow SSH port forwarding.
Countering SSH Tunneling Risks
Countering these risks requires the ability to monitor, control, and audit encrypted SSH connections. For preventing bouncing, it requires proper configuration and hardening of IoT operating systems. It is also important to only allow protocols that can be inspected through the firewall.
To counter these risks, certain measures can be implemented.
- Monitoring and Controlling SSH Usage: One of the most effective ways to counter SSH Tunneling risks is to monitor and control its usage. By limiting SSH access only to those who require it for their job functions, organizations can reduce the potential vectors for attack. Additionally, regular audits of SSH usage can help identify any unusual patterns or behaviors that might signify a security breach.
- Implementing Strong Authentication Methods: Using robust authentication methods such as two-factor authentication can significantly reduce the risk of unauthorized access through SSH Tunneling. This ensures that even if an attacker manages to obtain a user’s credentials, they would still need to bypass an additional layer of security.
- Regularly Updating and Patching SSH Software: Like any software, SSH software has vulnerabilities that can be exploited by attackers. Regularly updating and patching the software can fix these vulnerabilities, reducing the risk associated with SSH Tunneling.
- Restricting SSH Tunneling: In situations where SSH Tunneling is not required, it may be prudent to disable this feature altogether. This eliminates the possibility of any risks associated with it.
- Employ Intrusion Detection Systems (IDS): An IDS can monitor network traffic for suspicious activity associated with SSH Tunneling. If any such activity is detected, the system can alert administrators who can then take appropriate action.
By implementing these measures, organizations can significantly reduce the risks associated with SSH Tunneling. However, it’s important to remember that no measure is foolproof and a layered approach to security is always the best strategy.
How to Configure an SSH Tunnel
Configuring an SSH tunnel requires specific command line options and server configuration file settings. The exact process may vary depending on the specific software being used, but generally follows a similar structure.
# Example of SSH Tunnel Configuration
ssh -L local_port:remote_host:remote_port user@ssh_serverIn this example, the -L option specifies that connections to the given TCP port or Unix socket on the local (client) host are to be forwarded to the given host and port, or Unix socket, on the remote side.
Conclusion
SSH tunneling is a powerful tool with many important uses, particularly in corporate environments. However, it can also pose significant security risks if not properly managed and controlled.
Understanding what an SSH Tunnel is and how it works is the first step towards effectively leveraging its benefits and mitigating its risks.





