Cybersecurity is vital for any business to succeed. In today’s working environment, employees use smart devices or smartphones to work, but it poses a significant threat to the organization. However, most companies do not understand that cyber threat actors can take advantage of employee’s tech-savviness. And if they do not know how to identify threat actors, how will they guard against imminent threats?
Who/what are threat actors?
Threat actors can be a group or an individual that can cause damage your data security or business. Their intrinsic capability of causing harm, no matter their intentions, justifies the name threat actors.
Importance of identifying threat actors
Cyber incident planning and response are essential in any business to keep off threat actors. However, if you can’t identify your threat actors, you won’t understand their target area, abilities, and motivation. Identifying threat actors will help you allocate your resources to a relevant threat or risk effectively.
So, how do yo you identify threat actors? The idea is to have your information security professionals identify the possible threat actors. They should also determine who the individuals are, how and why they are targeting your network security, data integrity, and operations. Following these steps guarantees developing a solid response strategy and understanding more about the cyber threats that can impact a business.
Types of threat actors
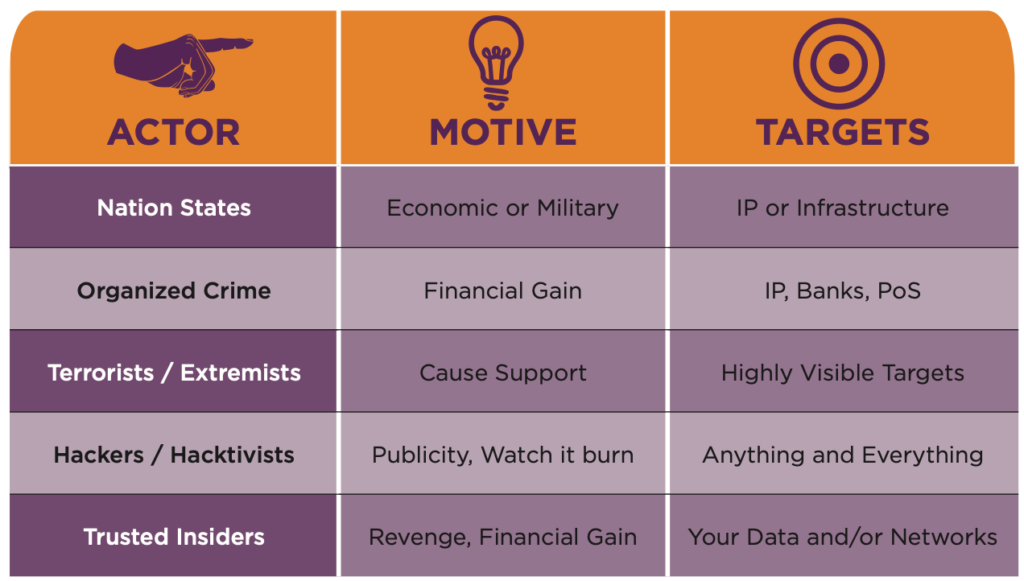
Hacktivists
Derived from the word hacker and activist, a Hacktivists’ mission is to inflict damage to a group or organization. Usually, it may be due to political reasons against a group that they oppose. Hacktivists may be a group or an individual.
Their attacks often use the same tools and techniques and also follow a similar pattern. They are determined to reach their goals and even garnering more resources to carry out their attack, thus, posing a severe threat to an organization.
Cybercriminals
Cybercriminals are organized crime attackers who engage in targeted attacks driven by profits. Meaning, they target areas that have a higher value, like banking information and personally identifiable information. Apart from that, they also engage in sophisticated ransomware attacks.
Disgruntled Insiders
Disgruntled insiders, also known as Inside Actors, are typically your disgruntled ex-employees or employees who are either looking for financial gain or revenge. They are one of the biggest threats because they know the internal operations and processes or direct access to your business-sensitive data.
Their activities are less likely known as they are less likely to trigger the red flag in an organization network. It isn’t easy to distinguish their activities from those that occur in the network regularly. However, with the right tools in place, disgruntled insiders can be found through security logs and audits.
Nation-State Actors
These threat actors are very powerful and are most likely funded by countries. They can carry out large scale attacks and advanced persistent threats(APTs). APTs are attacks that unauthorized users gain access to networks or systems for a certain period without being detected.
Their primary purpose is to maintain and infiltrate their presence in a network for a certain period to collect a targeted data type. The attack can move through a network and merge in with the regular traffic. That is one reason Nation-state actors are undetected for months and even years but causing severe damage an organization.
Also, their motivation does not come from financial gain. It lies in political espionage, national security, military intelligence, and influencing other nation’s political processes.
Careless Employees
Careless employees pose insider threats to an organization; they are the biggest target for attackers. Leaving a terminal or computer unlocked for a few minutes is enough for threat actors to gain access.
Other careless insider threats include exploiting naive or unaware employees via their personal devices or careless online behavior. Such exploits could grant attackers access to sensitive database files or proprietary information.
Conclusion
Once you have identified the threat actors, you have to ensure that your network is well equipped to handle these threats if one was to materialize. Make sure you implement the correct monitoring tool, set up an alerting system in case of network breaches, and collect activity logs.





